You are here: CSP Developer’s Guide: Overview > 11 Call Routing > Incoming Call Handling

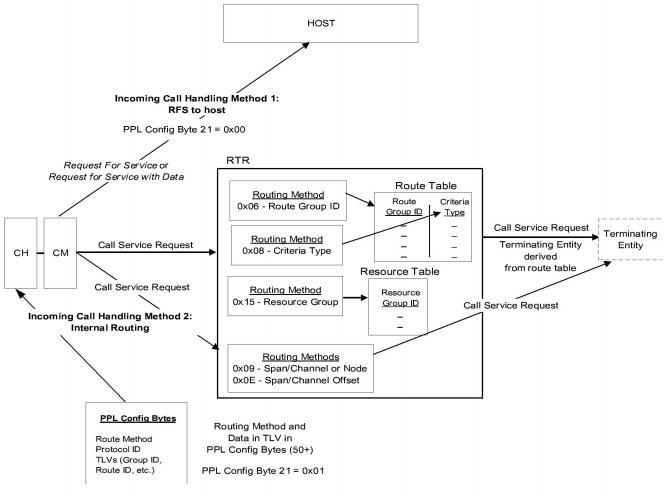
You can process incoming calls two ways:
• Send the Request For Service (or Request for Service with Data) message to the host This option is the system default.
• Use Internal Router
When the CH component receives a call, it sends a Call Service
Request (CSR) to the CM component, which forwards it to the
router. To configure the PPL Config Bytes of the CH component,
you must use the Router Protocol and Route Method TLVs, along
with other TLVs required for the specific route method.
The Route methods you can use include the following:
– Route Group (0x06)
– Criteria (0x08)
– Resource Group
If you choose to use Route Group (0x06) or Criteria (0x08), the
router uses the route table to find a terminating channel. If you use
the Resource Group method, the Resource Group table determines
the terminating channel. If you use any other route method, the
CSR from the CH component indicates the terminating entity.
When the terminating entity is derived, a CSR is sent to the remote CH component, and a connection is made. If a CSR ACK is not received within 3 minutes, the switch sends a Request For Service message. This is CH Timer 8 (Router Call Service ACK Wait), and you can use the PPL Timer Configure message to configure it.
To enable internal routing, set PPL Config Byte 21 of the CH component to 0x01
There are two methods for handling incoming calls, shown in Incoming Call Handling.
Figure 11-2 Incoming Call Handling

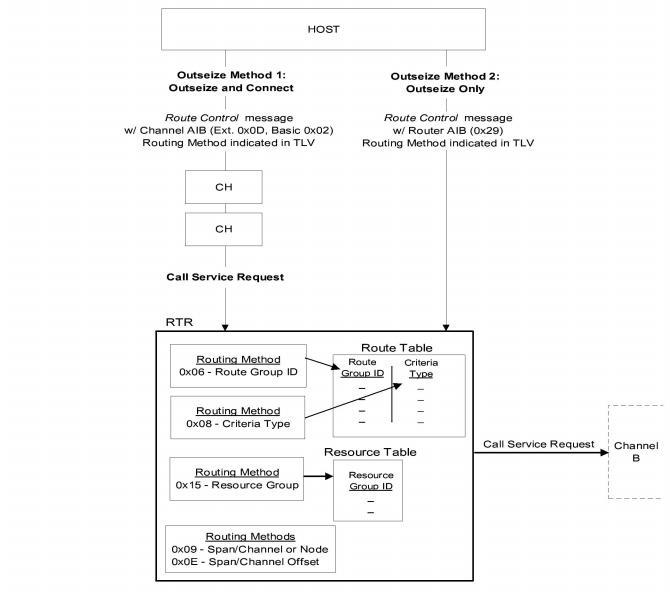
Host-Initiated Outseizures
Use the Route Control message to initiate inseizures. Use TLVs to indicate the Route Method and associated data.
Where Channel A is known, use the Channel AIB. When a terminating channel is derived, the two channels are connected.
If Channel A is not known, use the Route AIB. When a terminating channel is derived, it is seized and no further action is taken by the switch.
Important! For backward compatibility, you can also use the Outseize Control message if internal routing is not required. You specify the terminating channel in the message.
Figure 11-3 Host-Initiated Outseize Methods